Source - 2nd International Meeting: 3 Days Against Techno-Sciences – Italy, July 2020 2.3.2020 325nostate
This year too, we are proposing an informal, convivial and international opportunity for discussion and reflection among individuals and organisations engaged in building an analysis and a critique of what we may call the technoworld. A world which is going through an epoch-making paradigm shift, where all bodies and our very experience have become one of the most important new raw materials. Engineering of the living and digital control are increasingly replacing a large part of the previous market of commodities, which are becoming obsolete. On a planet which has been plundered well beyond its biological limits, the re-designing through synthetic biology and artificial reproduction in a eugenic key of human beings and their management represents the new path forward. This of course for those who will be included in the new power arrangement, for the others no plans have emerged, or perhaps the fact that they have not been presented is already an answer in itself, they will certainly not be satisfied with merely marginalising a part of the world.
For those who ask where the current system, based on systematic exploitation of the planet, can find a way to reorganise itself, incorporating into its discourse the farce of sustainability, the answer lies in taking over human beings themselves: managed, influenced and addressed in their behaviour so that they themselves produce processes which can turn them into commodities. This is the true essence of green and sustainable policies to save the planet from so many catastrophes, of which climate catastrophe is only a part. Human beings who will soon be genetically edited in a process of ongoing perfectibility, where the body will be seen as a limit to be overcome, where what is human will be considered an error, and must therefore continuously adapt to a machine world. A techno-scientific adaptability which will become the only possibility. We can now seem how the cybernetic paradigm, according to which “the environment we live in has always been so radically modified that today we are forced to modify ourselves”, takes a material and dramatic shape.
One of the main motors of this process is so-called artificial intelligence, increasingly pervasive, which does not impose is will by force, but is moving into every sphere of our existence, without giving us time to understand where and when this process began, and especially makes it superfluous or impossible to understand its more profound processes.
In these months, we have been seeing how quickly the 5G network is being launched in the world, and how this merely represents the beginning of the overwhelming flow of the internet of commodified bodies. We have also seen in China the management and control of millions of people through the 5G network and other surveillance technologies, in order to handle the quickly spreading Coronavirus contagion. Control and management on such a vast scale has never before been seen o attempted. An experiment which closely involves the international scientific milieu, the one that wears a white smock over camouflage: never has such a huge laboratory been thought of before, and the old form of totalitarianism, in a large part of the world, is fading off to make way to soft control and management of bodies, more effective however than repression and barbed wire. As supporters of artificial intelligence and their transhumanist fans have repeatedly announced, the real strength and power of these technologies lies in the fact that they intervene in dealing with the new and most critical challenges the planet will be facing in the near future. We have become used to war as a model for reinforcing power and creating and managing new markets. Today, there is also something new: a cybernetic and transhumanist paradigm which expresses itself through algorithms, often leaving it to these to solve problems, something which is blended in the lab with surprising efficiency, where apps and prescriptions dressed up as suggestions sent by smartphone in China have turned millions of people into sanitary prison guards of themselves.
Around us, profound transformations need to be understood, the analyses we make with the usual interpretations are limited and reductive, they are not able to grasp today’s transformations, power evolves and so must our analyses: this is the basis for undertaking and assigning priorities to fight for. How can one fight something one does not know? What one cannot understand? There are fundamental epochal shifts going on, shifts we need to understand. We have to see in which direction power is moving, before it fully implements its projects, so we do not come too late, and especially so they do not find us once again unprepared.
It is with this spirit that we are organising this year a second meeting, scheduled for the month of July, in order to involve organisations and individuals from various countries already engaged in a profound and clear analysis of the present, and actively involved in opposition to the developments of techno-sciences. An involvement which may break the glass window of inevitability through which too many stare passively at the course of events. A meeting to reinforce critical thinking in discussion with other organisations and individuals, who may follow different paths, but share a common desire to understand what is going on around us.
We shall focus on smart cities, 5G networks, artificial intelligence, transhumanism, artificial reproduction of human beings, genetic engineering and redesigning of living beings through synthetic biology.
The programme, place of meeting and exact dates will be made known shortly.
Since this meeting is entirely self-organised and with very limited means, please help us spread this text wherever there may be listening ears and burning hearts, worried about the near future which is already our present.
Collettivo Resistenze al Nanomondo
For information and contact:
www.resistenzealnanomondo.org, info@resistenzealnanomondo.org
PDF Second international meeting: [Eng], [It], translation to [Esp]
La Tarcoteca

Mostrando entradas con la etiqueta Internet. Mostrar todas las entradas
Mostrando entradas con la etiqueta Internet. Mostrar todas las entradas
viernes, 6 de marzo de 2020
lunes, 16 de abril de 2018
Defeating Facebook: Deleting is not the Answer
Source Defeating Facebook: Deleting is not the Answer - The Fifth Column 9.4.2018
by Joe Bear • April 9, 2018
 (TFC) – The internet is not free.
(TFC) – The internet is not free.
The internet is paid for by marketing and advertising, and many companies make a great deal of money off of their ability to collect, analyze, and sell data that is used in marketing. This is how Google, Facebook, and many other companies make the majority of their money. Others, such as Amazon, Target, Walmart, etc. also do it. Every time a company offers you a discount for the use of a membership card they are tracking your purchases and collecting data. In one notorious instance, Target’s algorithms were able to determine that a teenage girl was pregnant before her parents were even aware.
In the recent Cambridge Analytica scandal, many people just began to become aware of the beginning of how much data Facebook gathers, yet they do not yet understand the power of the deductive analysis upon their data. It seems that few people are aware that Facebook not only gathers and stores everything that you post on your public profile, but everything that you type into your browser, even if you never send it, and this information is combined with the data that Facebook gathers from the tracking cookies that it plants on your computer. Many websites across the internet will put these cookies on your computer, even if you are not a Facebook user.
What can you do? The cookies used by Facebook, and others that are out to gather data about you generally never expire, so you should never allow cookies to last beyond the end of session (you can change this in your browser settings). There are browser extensions that will also help prevent Facebook tracking, and other forms of data collection, and some malware. The extensions “Ublock Origin,” “Disconnect,” and “Privacy Badger” should be used by everyone, and more advanced users should also consider either “NoScript” for Firefox or “ScriptSafe” for Chrome.
In order to prevent Facebook’s gathering of all the information on your phone, like your contacts, call history, texting data, and who knows what else, and giving it essentially total control over everything on your mobile device, the simple answer is to avoid using the Facebook app if you have an Android device. Due to the way the iPhone works, it is not as prone to the blatant breach of privacy, so use at your own risk on iPhones, as you are relying on the IOS to prevent the data gathering.
If you wish to use Facebook to continue to maintain contact with others, yet you either wish to take back your privacy, or wish to have a higher degree of digital security, or maybe you are just tired of “Facebook jail” whenever a Facebook censor needs to make their daily quota, there is now a tool to allow that. Thanks to crypto-activist Patrick Smith there is now a browser extension for Chrome (with Firefox extensions in the works) that will allow you to make encrypted posts that only your preferred audience can see. All others will see only encrypted nonsense. Because it is a browser extension, it does all the work for you, and it is based on the cryptography of OpenPGP using 4096 bit RSA keys. In short, it is truly secure up until an end node compromise, arguably as secure as Signal messenger in its use of cryptographic primitives. A use case even for activists that make practically all of their posts public is the group encryption capability. This allows a group of like-minded persons to create a Facebook group and use it to communicate with others, but securely and privately. Only those within the group that have the group passphrase will be able to read the posts within the group. Even in the case that a person has their device seized by law enforcement, or Facebook turns over their data to law enforcement, or should your Facebook is accessed by a malicious third party, without the passphrase required for your FaceMask decryption no one can read anything that was encrypted by FaceMask.
Setup and use are simple, and even the less technically inclined persons can follow this simple video tutorial. Facebook cannot use data against you that it does not have. Stalkers, law enforcement, and others cannot use information that they do not have. Using this tool, your information will never be revealed to those who you do not wish to see it. The potential to communicate privately and securely across a widely used public platform is simply amazing, and activists, in particular, would be foolish not to take advantage of this new capability.
You can check out the website HERE and the Facebook page HERE. Get the Chrome extension HERE. Even deleting Facebook will not remove the data they have about you, and that alone will not stop their use of tracking cookies. Government regulations will not help you, if anything the Government is attempting to weaken encryption capabilities like this. It’s your privacy. It’s your security. It’s up to you to keep it private and secure. Crypto-anarchists, cypherpunks, and crypto activists of all stripes are here to help you do just that.
by Joe Bear • April 9, 2018
 (TFC) – The internet is not free.
(TFC) – The internet is not free.The internet is paid for by marketing and advertising, and many companies make a great deal of money off of their ability to collect, analyze, and sell data that is used in marketing. This is how Google, Facebook, and many other companies make the majority of their money. Others, such as Amazon, Target, Walmart, etc. also do it. Every time a company offers you a discount for the use of a membership card they are tracking your purchases and collecting data. In one notorious instance, Target’s algorithms were able to determine that a teenage girl was pregnant before her parents were even aware.
In the recent Cambridge Analytica scandal, many people just began to become aware of the beginning of how much data Facebook gathers, yet they do not yet understand the power of the deductive analysis upon their data. It seems that few people are aware that Facebook not only gathers and stores everything that you post on your public profile, but everything that you type into your browser, even if you never send it, and this information is combined with the data that Facebook gathers from the tracking cookies that it plants on your computer. Many websites across the internet will put these cookies on your computer, even if you are not a Facebook user.
What can you do? The cookies used by Facebook, and others that are out to gather data about you generally never expire, so you should never allow cookies to last beyond the end of session (you can change this in your browser settings). There are browser extensions that will also help prevent Facebook tracking, and other forms of data collection, and some malware. The extensions “Ublock Origin,” “Disconnect,” and “Privacy Badger” should be used by everyone, and more advanced users should also consider either “NoScript” for Firefox or “ScriptSafe” for Chrome.
In order to prevent Facebook’s gathering of all the information on your phone, like your contacts, call history, texting data, and who knows what else, and giving it essentially total control over everything on your mobile device, the simple answer is to avoid using the Facebook app if you have an Android device. Due to the way the iPhone works, it is not as prone to the blatant breach of privacy, so use at your own risk on iPhones, as you are relying on the IOS to prevent the data gathering.
If you wish to use Facebook to continue to maintain contact with others, yet you either wish to take back your privacy, or wish to have a higher degree of digital security, or maybe you are just tired of “Facebook jail” whenever a Facebook censor needs to make their daily quota, there is now a tool to allow that. Thanks to crypto-activist Patrick Smith there is now a browser extension for Chrome (with Firefox extensions in the works) that will allow you to make encrypted posts that only your preferred audience can see. All others will see only encrypted nonsense. Because it is a browser extension, it does all the work for you, and it is based on the cryptography of OpenPGP using 4096 bit RSA keys. In short, it is truly secure up until an end node compromise, arguably as secure as Signal messenger in its use of cryptographic primitives. A use case even for activists that make practically all of their posts public is the group encryption capability. This allows a group of like-minded persons to create a Facebook group and use it to communicate with others, but securely and privately. Only those within the group that have the group passphrase will be able to read the posts within the group. Even in the case that a person has their device seized by law enforcement, or Facebook turns over their data to law enforcement, or should your Facebook is accessed by a malicious third party, without the passphrase required for your FaceMask decryption no one can read anything that was encrypted by FaceMask.
Setup and use are simple, and even the less technically inclined persons can follow this simple video tutorial. Facebook cannot use data against you that it does not have. Stalkers, law enforcement, and others cannot use information that they do not have. Using this tool, your information will never be revealed to those who you do not wish to see it. The potential to communicate privately and securely across a widely used public platform is simply amazing, and activists, in particular, would be foolish not to take advantage of this new capability.
You can check out the website HERE and the Facebook page HERE. Get the Chrome extension HERE. Even deleting Facebook will not remove the data they have about you, and that alone will not stop their use of tracking cookies. Government regulations will not help you, if anything the Government is attempting to weaken encryption capabilities like this. It’s your privacy. It’s your security. It’s up to you to keep it private and secure. Crypto-anarchists, cypherpunks, and crypto activists of all stripes are here to help you do just that.
domingo, 15 de mayo de 2016
What is a VPN and do you need one
Discover how, with the help of VPN, you can watch movies that are blocked in your country, crack into websites that you don’t have access to, hide from the FBI when you download torrents and more.
VPN applications were originally designed for big organizations with more than one PC office.
Note: Go to the paragraph after the illustration if the technical explanation doesn’t interest you and you only want to know what can be done with VPN.
VPN is an acronym for Virtual Private Network.
Originally, VPN was used by large companies to connect computers in distant locations and until today, the use of VPN is popular among organizations with more than one PC office.
Imagine, for example, that the Coca-Cola Company in Atlanta has an office building where all of the computers are connected to the company’s server through cables, and there is little danger that hackers will break into Coca-Cola’s private network.
Now Coca-Cola opens an office in Canada and its employees in Toronto need access to the private network. But running a cable from the office in Atlanta to Toronto is a bit too much just to maintain privacy. Therefore the company uses a VPN to virtually create aprivate network (hence the acronym “Virtual Private Network” or VPN).
This is how a connection was formed between the computer in Toronto and the main server in Atlanta in a secure way (the different communication protocols of the VPN are responsible for the security, which is, of course, not as perfect as a real private network, but is close enough).
This connection that is established between these computers without any real cables is, of course, made through the internet. That is why, many workers (working from home, working from a hotel, or people commuting) can connect to Coca-Cola’s virtual private network as long as they have proper credentials.
Take a look at the illustration we made to demonstrate a VPN.
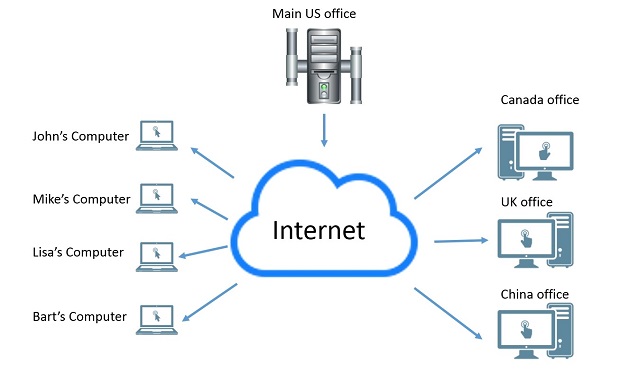
Anonymous surfing with VPN
In practice, although the above explanation refers to large organizations, VPN services have become popular due to their secondary feature: The ability to be seen as if you are surfing from the main server when you might actually be in a different country.
Since the entire communication between your computer and the VPN service is encrypted, neither Google, your internet service provider nor the Secret Service can find out which sites you actually visit, the emails you receive, etc. The entire communication looks as if it came out of the VPN’s main server, which is usually located in a different country and more importantly, this communication is encrypted.
There are two main audiences for VPN services:
- Regular people who simply want to surf anonymously, be it for security reasons, or the will to watch content over the internet that is blocked in their country (One of the common examples is Netflix which have restrictions in many countries).
- People who are active in grey or even in dark areas, such as users who want to watch porn and do not want their internet provider or Google to know about it (in some countries, this is a criminal act), terrorists dealing with weapons, criminals encrypting data about their activity, etc.
What can be done with VPN?
Some of the most common uses of VPN are listed below:
- Unblocking TV programs – VPN can serve for watching videos that are not available in the country you are in. For example, Hulu and Netflix movie services, British BBC series, Soccer matches and other sports that are broadcasted online for free only in certain countries.
- Unblocking sites – Some countries block services like Facebook, YouTube, Twitter and more. A VPN service allows you to be in China but lets you surf as if you are in the USA. Similarly, some schools and organizations block the access to popular sites and social networks and the solution to this is VPN.
- Torrents encryption – In some countries, downloading torrents is a criminal offense. In other countries, internet service providers detects that a user is downloading Torrents and slows down the surfing speed as a way of punishment. A VPN service encrypts the transmitted data so that even your internet service provider will not know you are downloading Torrents and therefore no punishment can be given.
- Hide identify – With VPN you can impersonate a user from a foreign country for a handful of reasons. (This is very useful in the internet community.)
a
xxxx
xxxx
xxxx
Recommended VPN services
Nowadays, numerous VPN services are available. It seems as if every website developer is maintaining servers in different countries and calling themselves a VPN service.
Nevertheless, load management (so that your surfing will not be slowed down because many people are using the server), the ability to slip past Netflix and its counterparts (that constantly try to detect the VPN services and block them) and more parameters create a distinction between these VPN services.
| Rank | Provider | Money Back Guarantee (Days) | Our Score | User Rating | More Info |
|---|---|---|---|---|---|
 |  | 30 | 5 | Read Review | Visit Site |
| 2 |  | 7 | 4.9 | Read Review | Visit Site |
| 3 |  | 30 | 4.8 | Read Review | Visit Site |
| 4 |  | 7 | 4.6 | Read Review | Visit Site |
| 5 |  | 30 | 4.5 | Read Review | Visit Site |
Important Note: We do not encourage you to perform illegal actions because you are using a VPN and can’t be caught. But we do encourage you to click on one of the social network buttons below, and share this article 

lunes, 25 de mayo de 2015
Open Internet Groups Launch the ‘Internet Health Test’
Free Press – Interactive tool lets users test their Internet speeds to detect Net Neutrality violations and safeguard the Web
WASHINGTON — On Tuesday, BattlefortheNet.com launched the “Internet Health Test” to collect data on Internet speeds across the Web. The test is an interactive tool that lets users run speed measurements across multiple interconnection points and collect data on whether and where Internet service providers are degrading online speeds and violating Net Neutrality.
Demand Progress, Fight for the Future and the Free Press Action Fund launched BattlefortheNet.com in 2014 and will ask more than a million members across the United States to run the Internet Health Test on their devices.
Anyone can take the test at: battleforthenet.com/internethealthtest/
In February the Federal Communications Commission voted to implement strong Net Neutrality protections, banning ISPs from blocking or throttling Internet users’ ability to connect to any website or service of their choosing. By letting users run continuous tests for the next three to six months, the Internet Health Test will amass data to determine whether ISPs are breaking the rules.
Researchers at Measurement Lab, an industry and research coalition, will evaluate the data. With the information the test yields, open Internet advocates will be able to identify potential violations and provide a strong benchmark for FCC enforcement of the open Internet rules.
“ISPs have long degraded speeds that Internet users paid for,” said Free Press Action Fund Internet Campaign Director Candace Clement. “Now that we have real Net Neutrality rules on the books we can hold companies like Comcast to account whenever they interfere with our speeds and mess with our content.”
“After repeatedly watching Internet service providers slow down people’s Internet connections we’re not going to just sit back and trust Comcast, Verizon and AT&T to follow the new open Internet rules,” said Fight for the Future Campaign Manager Charlie Furman. “The Internet Health Test is our way of sending a message to ISPs everywhere that we’re watching and we won’t let anyone throttle the Internet.”
Suscribirse a:
Entradas (Atom)

